12 Cross-Account DR, Backup, and Recovery
With cross-account backup and recovery, you can easily copy backups between accounts as part of the disaster recovery process.
Available only in Standard, Advanced, and Enterprise Editions, N2W's cross-account functionality allows you to automatically copy snapshots between AWS accounts as part of the DR module. With cross-region DR, you can copy snapshots between regions as well as between accounts and any combination of both. In addition, you can recover resources (e.g., EC2 instances) to a different AWS account even if you did not copy the snapshots to that account. This cross-account functionality is important for security reasons.
The ability to copy snapshots between regions can prove crucial if your AWS credentials have been compromised and there is a risk of deletion of your production data as well as your snapshot data. N2W utilizes the snapshot share option in AWS to enable copying them across accounts. Cross-account functionality is currently supported only for EC2 instances, EBS volumes, and RDS instances, including Aurora.
Cross-account functionality is enabled for encrypted EBS volumes and instances with encrypted EBS volumes and RDS databases.
FSx types need to be encrypted with a custom key.
Supported cross-region FSx types are Lustre, Windows, and OpenZFS.
Supported cross-account FSx types are Lustre (Persistent, HDD), Windows, and OpenZFS
Backup and DR vaults need a custom key.
Users will need to share the encrypted key used for the encryption of the volumes or instances to the other account as N2W will not do it.
In addition, N2W expects to find a key in the target account with the same alias as the original key (or just uses the default key).
For information on sharing encryption keys between different accounts, see https://n2ws.zendesk.com/hc/en-us/articles/28815492111005-Use-custom-KMS-encryption-keys-for-cross-region-cross-account-DR
If a matching encryption key is not found with an alias or with custom tags, the behaviour of the backup depends on the setting in the Encryption Key Detection list in the Security & Password tab of the General Settings screen:
Use Default Key – If the encryption key is not matched, the default encryption key is used.
Strict – DR encryption key must match, either with an alias or a custom tag.
Use Default Key & Alert – Use the default key and send an alert.
N2W can support a DR scheme where a special AWS account is used only for snapshot data. This account’s credentials are not shared with anyone and used only to copy snapshots. The IAM credentials used in N2W can have limited permissions that do not allow snapshot deletion.
N2W will tag outdated snapshots instead of deleting them, allowing an authorized user to delete them separately using the EC2 console or a script. The tag cpm_deleted will have a value of ‘CPM deleted this snapshot (<time-of-deletion>)’. Also, you may choose to keep the snapshots only in the vault account and not in their original account. This will allow you to save storage costs and utilize the cross-recovery capability to recover resources from the vault account back to the original one.
12.1 Configuring Cross-Account Backup
Once you have created an account with the Account Type DR, you can configure cross-account DR from the DR tab of a policy.
Cross-account fields will be available only if your N2W is licensed for cross-account functionality. See the pricing and registration page on our website to see which N2W editions include cross-account backup and recovery.
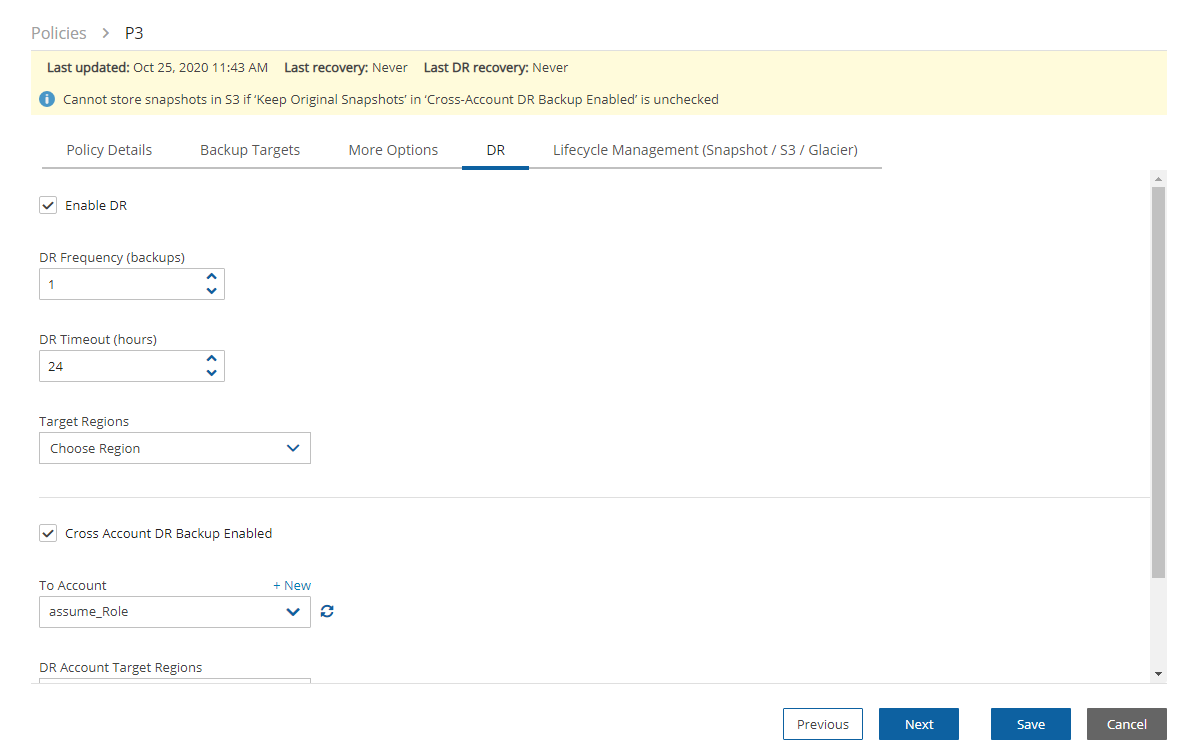
Once you select Cross-Account DR Backup Enabled, other fields become visible:
To Account – Which account to copy the snapshots to. This account needs to have been defined as a DR Account Type in the Accounts screen.
DR Account Target Regions – Which region or regions you want to copy the snapshots of the policy to. To include all Target Regions selected for backup, select Original in the list. Select additional regions as needed.
Keep Original Snapshots – Enabled by default, the original snapshot from the source region will be kept. If disabled, once the snapshot is copied to the DR account, it will be deleted from the source region.
Keep Original Snapshots must be enabled for Copy to S3 for Cross-Account DR Backup.
12.2 Cross-Account DR and Clean-Up
N2W performs clean-up on backup policies and deletes backups and snapshots that are out of the retention window, according to the policy’s definition. By default, N2W will clean up snapshots copied to other accounts as well. However, if you do not wish for N2W to clean up, because you want to provide IAM credentials that are limited and cannot delete data, you have that option. If you defined the DR account with Allow Deleting Snapshots set as False, N2W will not try to delete snapshots in the DR account. It will rather flag a snapshot for subsequent deletion by adding a tag to the snapshot called cpm_deleted. The tag value will contain the time when the snapshot was flagged for deletion by N2W.
When using this option, occasionally make sure that these snapshots are actually deleted. You can either run a script on a schedule, with proper permissions or make it delete all snapshots with the tag cpm_deleted. Or, using the EC2 console, filter snapshots by the tag name and delete them.
12.3 Cross-Account with Cross-Region
If you configure the backup policy to copy snapshots across accounts as well as across regions, be aware of how the increased number of copies might affect your AWS costs.
Cross-account with cross-region DR with AMIs is supported.
12.3.1 RDS Cross-Account with Cross-Region Recovery
AWS limits RDS snapshot cross-account copy to the DR account in the original region. To overcome this limitation, N2W performs two snapshot copies during the DR process:
Copy from 'Backup account - origin region' to ‘DR account - origin region'.
Copy from 'DR account - origin region' to ‘DR account - DR region'.
To ensure incremental snapshot copies across regions, enable Keep Original Snapshots on the Policy DR tab. If ‘Keep Original Snapshots’ is not enabled, then the cross-region copies will be full copies of the database.
In most usage scenarios, it is more cost efficient to enable Keep Original Snapshots. Incremental copies will use less space in the aggregate, reduce cross-region data transfer costs, and reduce Recovery Time Objective.
12.4 Cross-Account Recovery
If you have cross-account functionality enabled in your N2W license, and even if you configured N2Wto copy snapshots between accounts, you can recover across accounts. This is already mentioned in Recovery section 10. You need to choose which account to recover the resource (EC2 instance, EBS volume, or RDS database) to.
Only account type DR may be the target of a cross-account recovery.
When copying snapshots between accounts and not keeping the original snapshots, you will also have the option to restore the instance/volume to the original account. N2W will utilize the AWS share snapshot option to enable recovering resources across accounts.
Was this helpful?

