Appendix A -Recommended Configuration for Copy to S3
This section describes considerations when configuring Copy to S3 and how to create a VPC S3 endpoint.
A.1 Considerations When Configuring Copy to S3
A.1.1 Choosing a Storage Type
When creating a policy with the S3 option enabled, N2W will manage the lifecycle according to the policy settings. When configuring S3, consider the differences in the storage types:
Snapshot – The fastest option. It enables free recovery within seconds, but it has the highest storage cost. Snapshot is useful for backups that you need to recover quickly and keep for a short time.
S3 Storage – Provides much cheaper storage costs, but recovery is slower and costs a little more. S3 Storage is useful for backups that do not need quick recovery time and that you want to keep for a long time.
Glacier – Provides the cheapest storage costs, but recovery is the most expensive and the slowest. Glacier is useful for backups that you need to keep for several decades for compliance purposes and which you don’t expect to have to recover urgently.
N2W does not support File Level Recovery from Glacier.
A.1.2 Bucket Location
When configuring Copy to S3, consider the following when deciding where to put your S3 buckets:
Having the bucket in a different region then the target snapshot will incur AWS cross-region charges and will also result in slower copy speed due to the greater physical distance.
Putting the bucket in the same region as your protected resources will:
Help avoid cross-region data charges by AWS.
Help make the copy faster.
One bucket for all regions makes for easier management, while one bucket per region makes for optimal cost.
Since each AWS S3 bucket has some performance limits, configuring an AWS S3 Repository per policy will result in faster and more stable copies to S3. Or, if several policies are all writing to the same bucket, you can stagger the copies to avoid putting too much load on the same bucket at the same time.
A.1.3 VPC S3 Endpoint and VPC Peering
Using VPC endpoint enables instances to use their private IP to communicate with resources in other services, such as S3, within the AWS network without incurring network transfer fees.
You can set up a VPC S3/EBS endpoint in the VPC where the S3 worker is launched to make sure that the communication from the worker will be over private IP. Using an VPC S3 Endpoint can help avoid NAT costs (if used in the VPC) as there is no data processing or hourly charges for using Gateway Type VPC endpoints. Additionally, the copy process will be more secure as the communication will be over private IP, and the copy speed over the S3 Endpoint should be faster than over the Internet.
If the bucket is in another region or in another account, the transport charges will be incurred anyway.
In addition, you can set up VPC peering between the worker VPC and the N2W server VPC so that communication between the worker and the server will also be routed over private IP.
A.1.4 KMS Keys for the Bucket
When creating the S3 bucket in AWS, you have 2 encryption options:
SSE-S3 server-side encryption with Amazon S3-managed keys. This option is free, but it is less secure than SSE-KMS.
SSE-KMS server-side encryption with AWS KMS. This option has a cost per request, but it is more secure than SS3-S3.
When setting up the bucket, consider whether the free option (SSE-S3) is sufficient for your use case, or if you need greater security with SSE-KMS, which is more expensive.
A.2 Creating a VPC S3 Endpoint
1. In AWS, create a subnet within the VPC of the region.

After successful creation, the successful creation message appears.

The subnet is automatically associated with the default route table.
2. Create a new route table.

3. Change the subnet association by associating the previously created subnet with this route table. 4. Create a VPC endpoint for S3 in the region and associate it with the previously created route table.

5. Choose a region.
6. Then choose the previously defined route table. The permissions to access the bucket will be defined by the IAM policies attached to the roles of N2W.
7. Grant Full Access.

The route table of the subnet now looks like the following:

8. If N2W is in a different account/region/VPC, add an Internet Gateway to the route table so the ‘worker’ can communicate with N2W.
1. Add the following rule:

The route table will look like:

2. In this configuration, the connection to S3 will be routed to the VPC endpoint. See the example below:

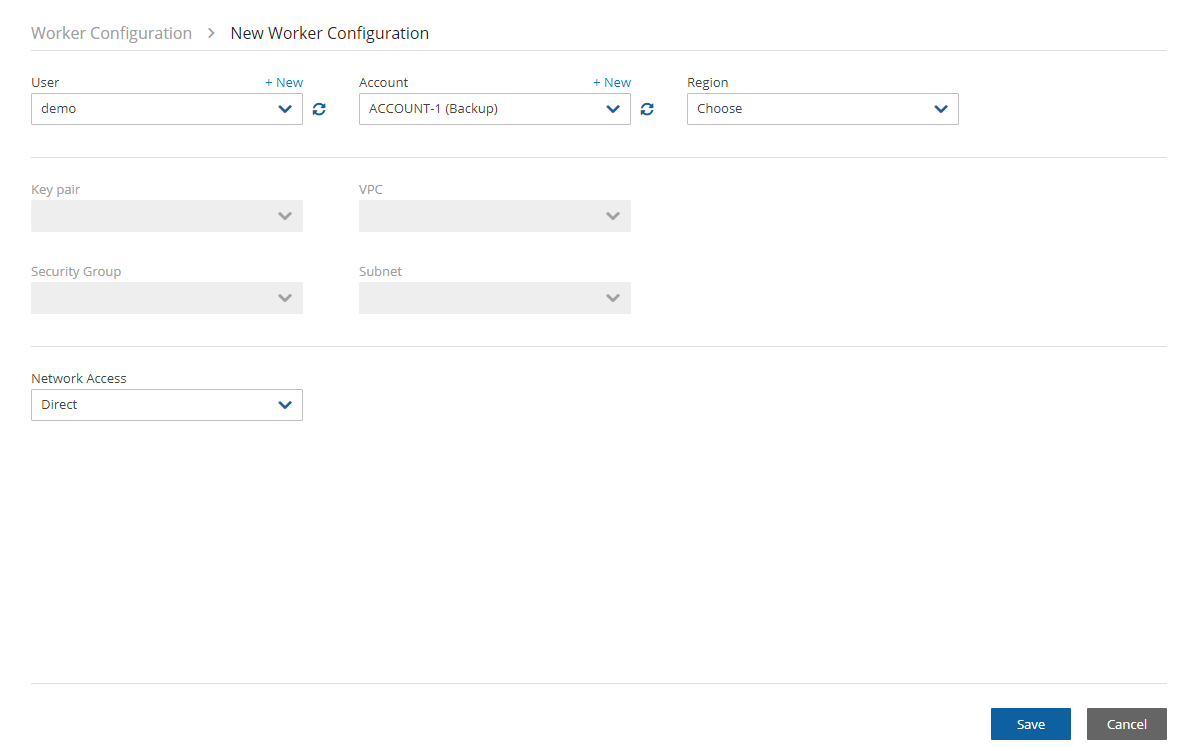
9. In N2W, select the Worker Configuration tab.
1. Select ![]() New.
2. Configure the worker to use this subnet in the specific region and the VPC where it is defined.
New.
2. Configure the worker to use this subnet in the specific region and the VPC where it is defined.
For additional information about setting up VPC Gateway Endpoints, see https://docs.aws.amazon.com/vpc/latest/userguide/vpce-gateway.html
Was this helpful?

