14 Tag-based Backup Management
N2W's tag-based backup management allows you to automatically fine-tune functionality.
Cloud and specifically AWS, is an environment based largely on automation. Since all the functionality is available via an API, scripts can be used to deploy and manage applications, servers, and complete environments. There are very popular tools available to help with configuring and deploying these environments, like Chef and Puppet.
N2W allows configuring backup using automation tools by utilizing AWS tags. By tagging a resource, such as EC2 instance, EBS volume, EFS, DynamoDB, or RDS instance, N2W can be notified of what to do with this resource without using the UI.
To tag Aurora clusters, tag one of the cluster’s DB instances, and N2W will pick it up and back up the entire cluster.
Since tagging is a basic functionality of AWS, it can be easily performed via the API and scripts. For more information on using the API or scripts, see https://docs.aws.amazon.com/AmazonRDS/latest/AuroraUserGuide/USER_Tagging.html
N2W supports both cpm backup and cpm_backup tags (section 14.1) and custom tags (section 14.2).
For Azure, the following options are not currently supported:
Custom tag
Exclude disk
Application awareness
For information on using tags with Resource Control, see section 15.5.
14.1 The 'cpm backup' and 'cpm_backup' Tags
To automate backup management for a resource, you can add a tag to that resource named cpm backup (or cpm_backup).The tag is lower case with a space or an underscore. N2W will identify this tag and parse its content. In this tag you will be able to specify whether to:
Ignore the resource and remove it from all backup policies.
Add the resource to a policy or list of policies.
Create a new policy, based on an existing one (template), and then add the resource to it.
The policy name on the cpm backup or cpm_backup tag is case sensitive and should be aligned with the policy name create on CPM.
If an AWS resource has 2 AWS tags with the same tag name, differing only by the case of the letters (upper, lower), then N2W will back up just one tag. The tag name will be in the format of the first tag N2W scans, and the tag value may be from the second tag. Check that tag names are in the same case.
Following is a summary table of all cpm backup and cpm_backup tag values:
Purpose
cpm backup cpm_backup Tag Value
Examples/Values
Set backup options for EC2 instances. See 14.1.3.
only-snaps (create AMIs without reboot)
initial-ami
only-amis
only-amis-reboot (create AMIs with reboot)
app-aware (Windows instance backup agent is same as snapshot and AMI options)
app-aware-vss (Enable application consistent with VSS)
app-aware-script (Enable application consistent without VSS)
policy1#only-snaps
new_policy:existing_policy#only-amis
policy1#initial-ami#app-aware
Set backup options for EFS instances. N2W will override EFS configuration with tag values. See 14.1.4.
vault role_arn cold_opt
cold_opt_val exp_opt
exp_opt_val
Default (example) ARN of role Lifecycle transition: N, D, W, M, Y Integer for D,W,M,Y only When resource expires: P (Policy Gen), N, D, W, M, Y Integer for D, W, M, Y only
Exclude volumes from backup. See 14.1.6.
policy1#exclude
Note: Tagged instances are excluded from the Exclude volumes option in General Settings for Tag Scan. Tagged instances are only excluded with the ‘#exclude’ tag.
policy1#exclude policy2#exclude
14.1.1 Adding to a Policy or Policies
To add a resource (e.g., an EC2 instance) to an existing backup policy, all you need to do is to create the tag for this resource and specify the policy name. For example:
policy1: key:cpm backup, value:policy1 or key:cpm_backup, value:policy1 or
policy1: key:cpm_backup, value:policy1 or key:cpm_backup, value:policy1
To add the resource to multiple policies all you need to do is to add a list of policy names, separated by spaces: policy1 policy2 policy3
You can add an RDS target using the tag scan, but the resource will be added without the connection parameters. After the tag scan, you will need to configure the Connection Details in the policy manually. See https://n2ws.zendesk.com/hc/en-us/articles/28878303166365--AWS-Read-Only-user-for-RDS-to-S3-feature
14.1.2 Creating a Policy from a Template
To create a new policy and to add the resource to it, add a new policy name with a name of an existing policy which will serve as a template (separated by semicolon): tag value: new_policy1:existing_policy1
You can also add multiple policy name pairs to create additional policies or create a policy (or policies) and to add the resource to an existing policy or policies.
When a new policy is created out of a template, it will take the following properties from it:
Number of generations
Schedules
DR configuration
Script/agent configuration
Retry configuration
It will not inherit any backup targets, so you can use a real working policy as a template or an empty one.
For Script definitions:
If backup scripts are defined for the template policy, the new one will keep that definition but will not initially have any actual scripts. You are responsible to create those scripts. Since the N2W server is accessible via SSH you can automate script creation. In any case, since scripts are required, the backups will have a failure status and will send alerts, so you will not forget about the need to create new scripts.
For Windows instances with a backup agent configured:
If that was the configuration of the original policy, the new instance (assuming it is a Windows instance) will also be assigned as the policy agent. However, since it does not have an authentication key, and since the agent needs to be installed and configured on the instance, the backups will have a failure status. Setting the new authentication key and installing the agent needs to be made manually.
Auto Target Removal for the new policy will always be set to yes and alert, regardless of the setting of the template policy. The basic assumption is that a policy created by a tag will automatically remove resources that do not exist anymore, which is the equivalent as if their tag was deleted.
14.1.3 Setting Backup Options for EC2 Instances
When adding an instance to a policy, or creating a new policy from template, you may make a few decisions about the instance:
To create snapshots only for this instance.
To create snapshots with an initial AMI.
To schedule AMI creation only.
If this option is not set, N2W will assume the default:
Snapshots only for Linux.
Snapshots with initial AMI for Windows instances by adding a backup option after the policy name. The backup option can be one of the following values:
only-snaps
initial-ami
only-amis
only-amis-reboot
For example, with an existing policy:
policy1#only-snaps, or for a new policy based on template and setting AMI creation:my_new_policy:existing_policy#only-amis
The only-amis option will create AMIs without rebooting them. The option only-amis-reboot will create AMIs with reboot.
For a Windows instance, you can also define backup with app-aware, i.e., a backup agent. It is used the same as the snapshots and AMI options.
When adding the app-aware option, the agent is set to the default: VSS is enabled and backup scripts are disabled.
app-aware-vss - Enable application consistent with VSS.
app-aware-script - Enable application consistent without VSS.
Additional configurations need to be made manually, and not with the tag.
You can also combine the backup options: policy1#initial-ami#app-aware
14.1.4 Setting Backup Options for EFS Instances
EFS can be configured by creating the cpm backup (cpm_backup) tag with the following values. In this case, N2W will override the EFS configuration with the tag values:
Key
Value
vault
Vault. Example: Default
role_arn
ARN of role. Example: arn:aws:iam::040885004714:role/service-role/AWSBackupDefaultServiceRole
cold_opt
Lifecycle transition:
N – Never M – Months
D – Days Y – Years
W – Weeks
cold_opt_value
Integer for D, W, M, Y only
exp_opt
When does resource expire:
P – Policy Generations W – Weeks
N – Never M – Months
D – Days Y – Years
exp_opt_val
Integer for D, W, M, Y only
Example:
N2W will back up EFS to the default vault, and set its expiration date to 1 day.
The max length for the cpm backup(cpm_backup) value is 256 characters.
14.1.5 Tagging a Resource to be Removed from All Policies
By creating the cpm backup(cpm_backup) tag with the value no-backup (lower case), you can tell N2W to ignore the resource and remove this resource from all policies. Also, see section 14.1.
14.1.6 Excluding Volumes from Backup
N2W can exclude a volume from an instance that is backed up on policy using the cpm backup(cpm_backup) tag with #exclude added to the end of the policy name value.
Add a tag to an instance that you want to back up:

Add a tag to volumes that you would like to exclude from being backed up:

For example, if instance1 has 3 volumes and has a cpm backup(cpm_backup) tag with the value policy1, adding the cpm backup(cpm_backup) tag with value policy1#exclude to a volume will remove it from the policy.
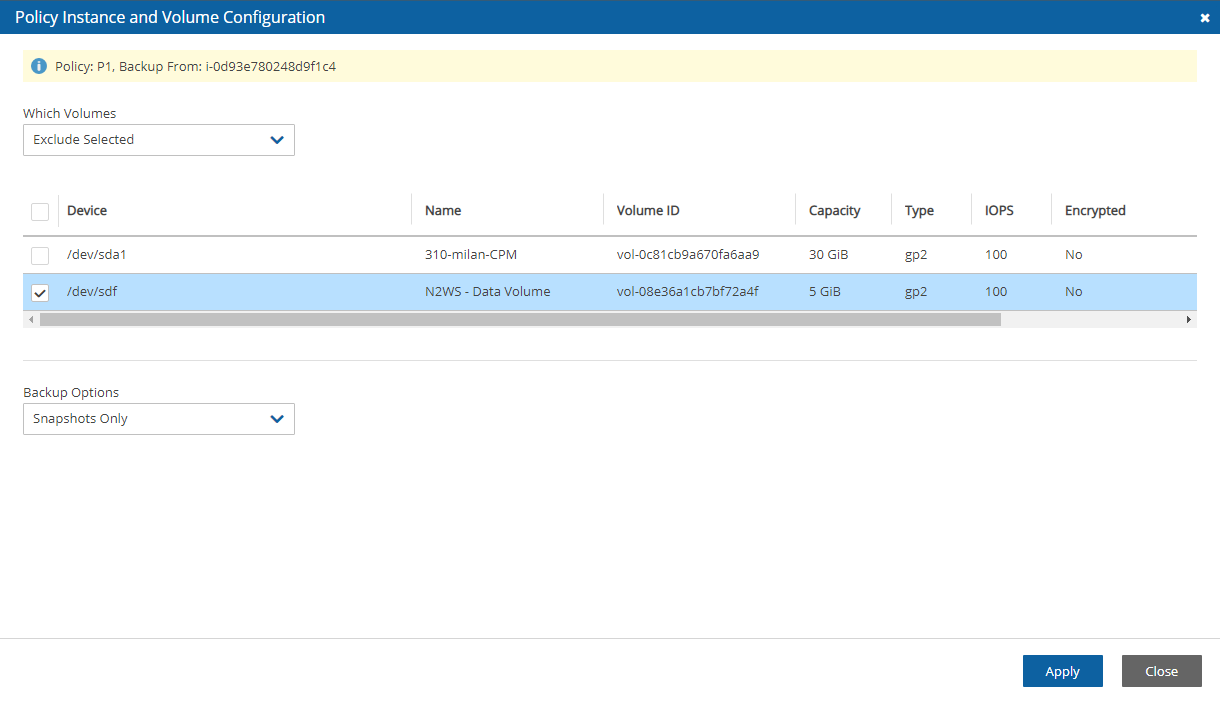
The instance with the excluded volume(s) will be added automatically as a backup target to the policy, after running Scan Tag.
Tagged instances are not included in the Exclude volumes option in the Tag Scan tab of General Settings and are excluded from backup only when tagged with #exclude for the policy.
14.2 Custom Tags
Custom Tags allow N2W users to easily backup resources using any tag of their choice.
You can define any number of Custom Tags on a Policy definition.
Custom tags take precedence over
cpm backup(cpm_backup) tags if both exist on a server.Define Custom Tags with the Names and Values to match the Tags of AWS Resources to add to the Policy.
If a user-defined Custom Tag exists on an AWS resource, the resource will be automatically added to the Policy during the Tag Scan process. See section 14.3.
It is possible to match an AWS Resource Tag with an N2W Tag Name or Value defined as a Prefix. For example, if the Tag Name ‘Department’ is defined as a Prefix, the following AWS resources that have a Tag Name starting with ‘Department’ will be added to the policy: ‘Department A’, ‘Departments’, and Department_3’.
Custom Tags are case-sensitive.
If the
cpm backup(cpm_backup) tag is used on a resource withno-backup, Custom Tags will be ignored and the resource will not be backed up.When the
cpm backup(cpm_backup) tag and a custom tag on a resource point to the same policy name, the custom tag will be ignored.
To see which resources were added to back up, open the Tag Scan log (Show Log), and look for a Custom Tags match.
To create Custom Tags:
In the Policies tab, select a policy.
Select the More Options tab.
Turn on the Custom Tags toggle.
Select
 New.
New.Define the Tag Name and Tag Value.
If relevant, select Name is Prefix and/or Value is Prefix.

14.3 Tag Scanning
Tag scanning can only be controlled by the admin/root user. When the scan is running, it will do so for all the users in the system but will only scan AWS accounts that have Scan Resources enabled. This setting is disabled by default. N2W will automatically scan resources in all AWS regions.
In the General Settings tab, select the Tag Scan tab.
Select Scan Resources.
In the Tag Scan interval list, set the interval in hours for automatic scans.
To override the exclusion of volumes specified in the UI and to exclude instances tagged with
#excludefor the policy, select Exclude volumes. See section 9.6.Select Save.
To initiate a tag scan immediately, select Scan Now.
To view the Last Scan, select Show Log.
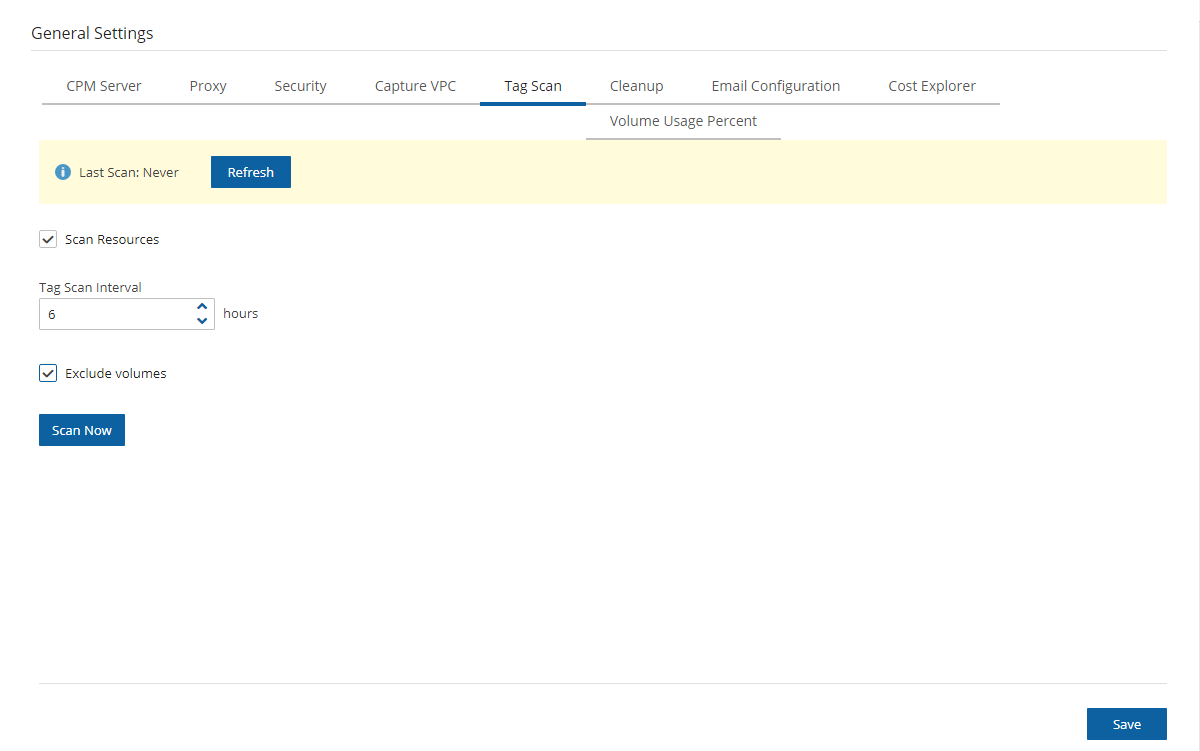
Even if scanning is disabled, selecting Scan Now will initiate a scan.
If you do want automated scans to run, keep scanning enabled and set the interval in hours between scans using the General Settings screen. You will also need to enable Scan Resources for the relevant N2W Accounts. See section 3.1.2.
14.4 Pitfalls and Troubleshooting
The following topics should help guide you when developing tags.
14.4.1 Pitfalls
There are potential issues you should try to avoid when managing your backup via tags:
The first is not to create contradictions between the tags content and manual configuration. If you tag a resource and it is added to a policy, and later you remove it from the policy manually, it may come back at the next tag scan. N2W tries to warn you from such mistakes.
Policy name changes can also affect tag scanning. If you rename a policy, the policy name in the tag can be wrong. When renaming a policy, correct any relevant tag values.
When you open a policy that was created by a tag scan to edit it, you will see a message at the top of the dialog window: “* This policy was automatically added by tag scan”.
Even if all the backup targets are removed, N2W will not delete any policy on its own, since deletion of a policy will also delete all its data. If you have a daily summary configured (section 17.5), policies without backup targets will be listed.
If the same AWS account is added as multiple accounts in N2W, the same tags can be scanned multiple times, and the behaviour can become unpredictable. N2W Software generally discourages this practice. It is better to define an account once, and then allow delegates (section 18.4) access to it. If you added the same AWS account multiple times (even for different users), make sure only one of the accounts in N2W has Scan Resources enabled in N2W.
14.4.2 Troubleshooting
Sometimes you need to understand what happened during a tag scan, especially if the tag scan did not behave as expected, such as a policy was not created. In the General Settings screen, you can view the log of the last tag scan and see what happened during this scan, as well as any other problems, such as a problem parsing the tag value, that were encountered. Also, if the daily summary is enabled, new scan results from the last day will be listed in the summary.
Ensure tag format is correct. Tips for ensuring correct tag formats are:
When listing multiple policy names, make sure they are separated by spaces.
When creating new policy, verify using a colon ‘
:’ and not a semi-colon ‘;’. The syntax isnew_policy1:existing_policy1.Use a valid name for the new policy or it will not be created. An error message will be added to scan log.
Use correct names for existing/template policies.
Resource scanning order is NOT defined, so use policy names as existing/template only if you are sure that it exists in N2W defined manually or scanned previously.
Was this helpful?

