20 Configuring N2W with CloudFormation
You can model and manage your infrastructure resources with AWS CloudFormation.
The process to configure N2W to work with CloudFormation is a single stream that starts with subscribing to N2W on the Amazon Marketplace and ends with configuring the N2W server.
N2W provides several editions, all of which support CloudFormation.
An IAM role will automatically be created with minimal permissions and assigned to the N2W instance.
Configure CPM with CloudFormation will fail where the requested Instance type is not supported in the requested Availability Zone. Retry your request, but do not specify an Availability Zone or choose us-east-1a, us-east-1b, us-east-1c, us-east-1d, or us-east-1f.
Search for N2W Software.
Select the AWS Free Trial & BYOL CPM edition, and then select View purchase options.
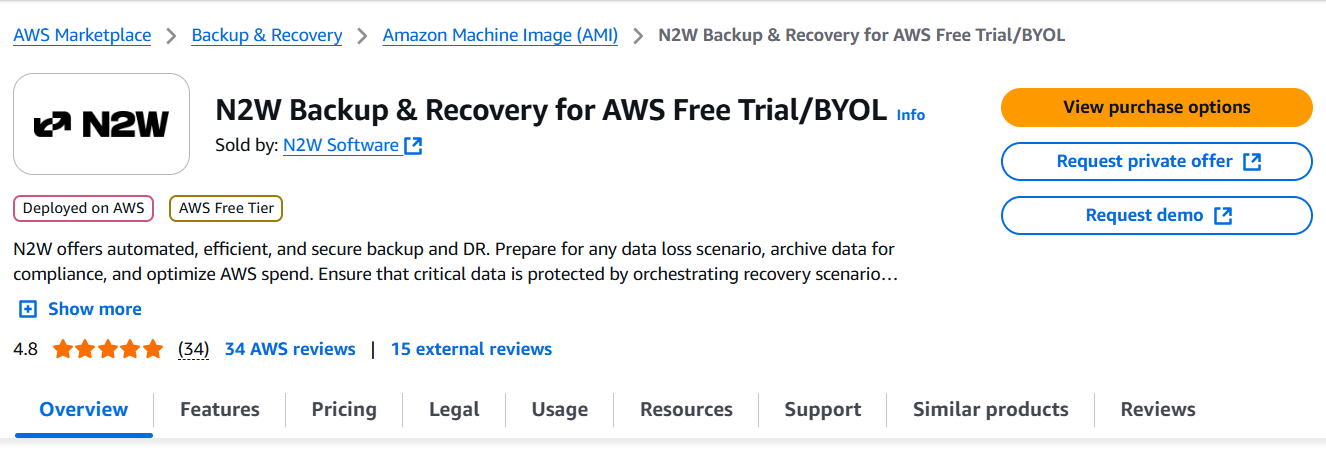
4. After reviewing the Overview, select View purchase options again.
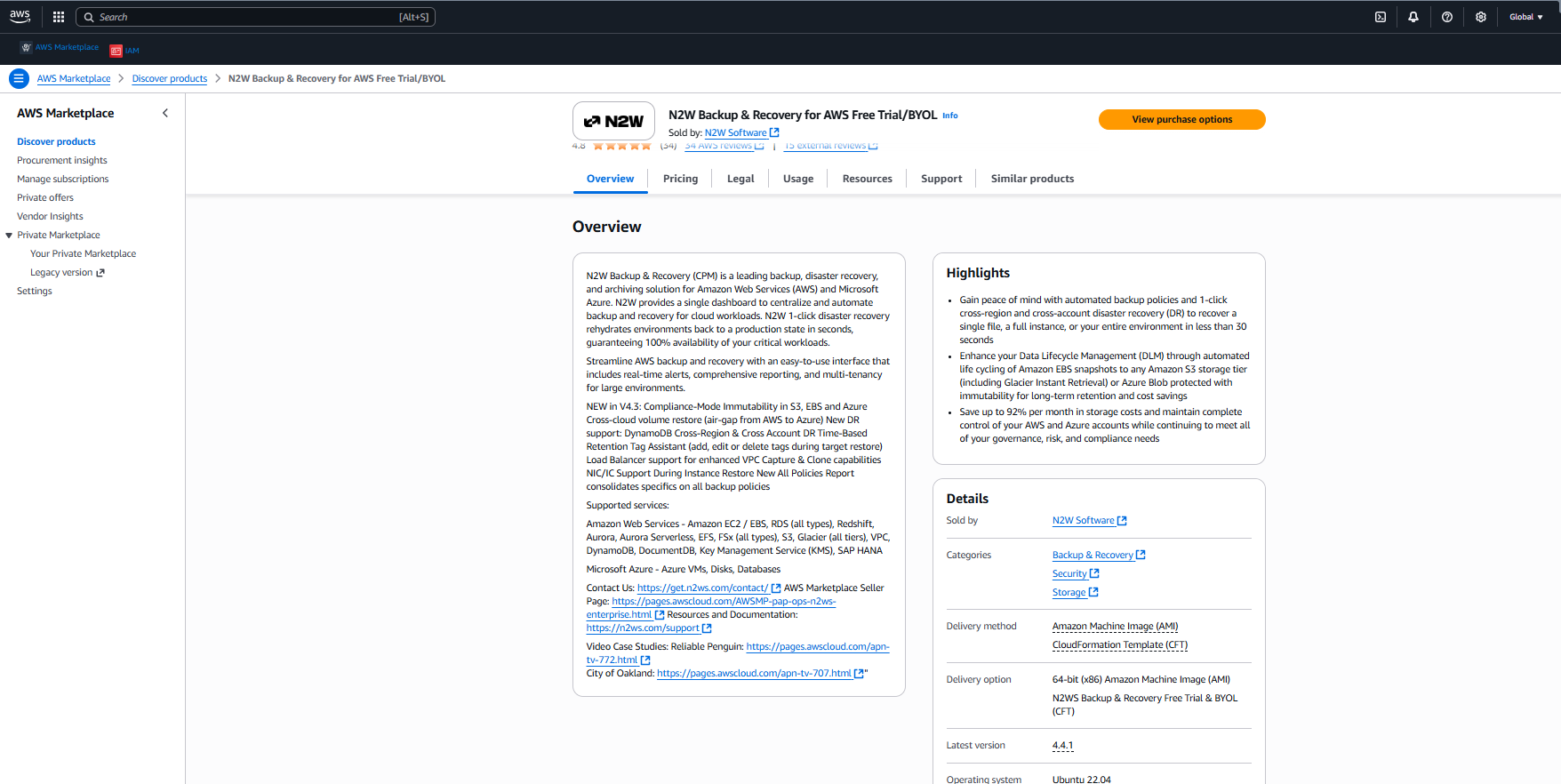
5. After purchasing N2W Backup & Recovery for AWS Free Trial/BYOL, select Launch your software.
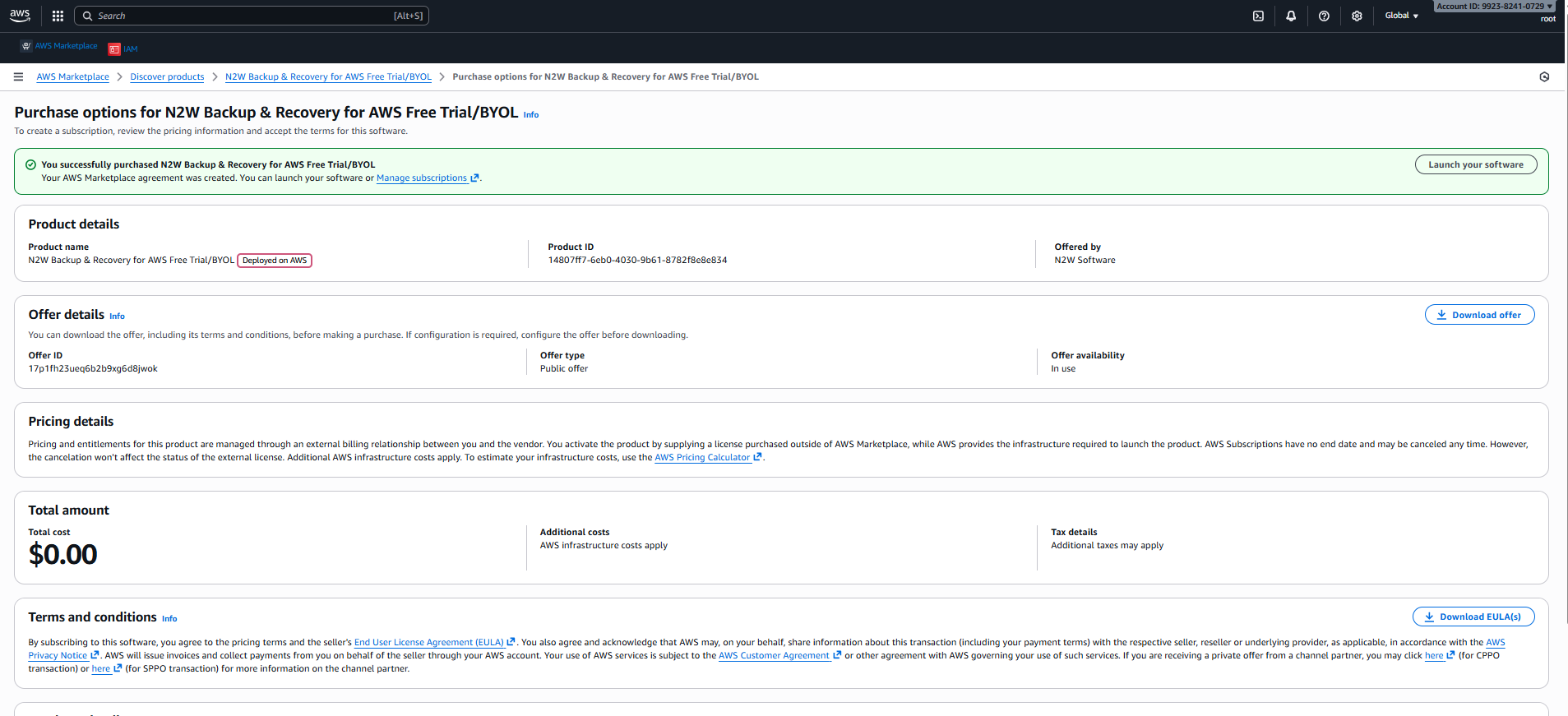
6. In the Setup section, select AWS CloudFormation for the Service. Select the relevant Version and Region, and then select Launch with CloudFormation.
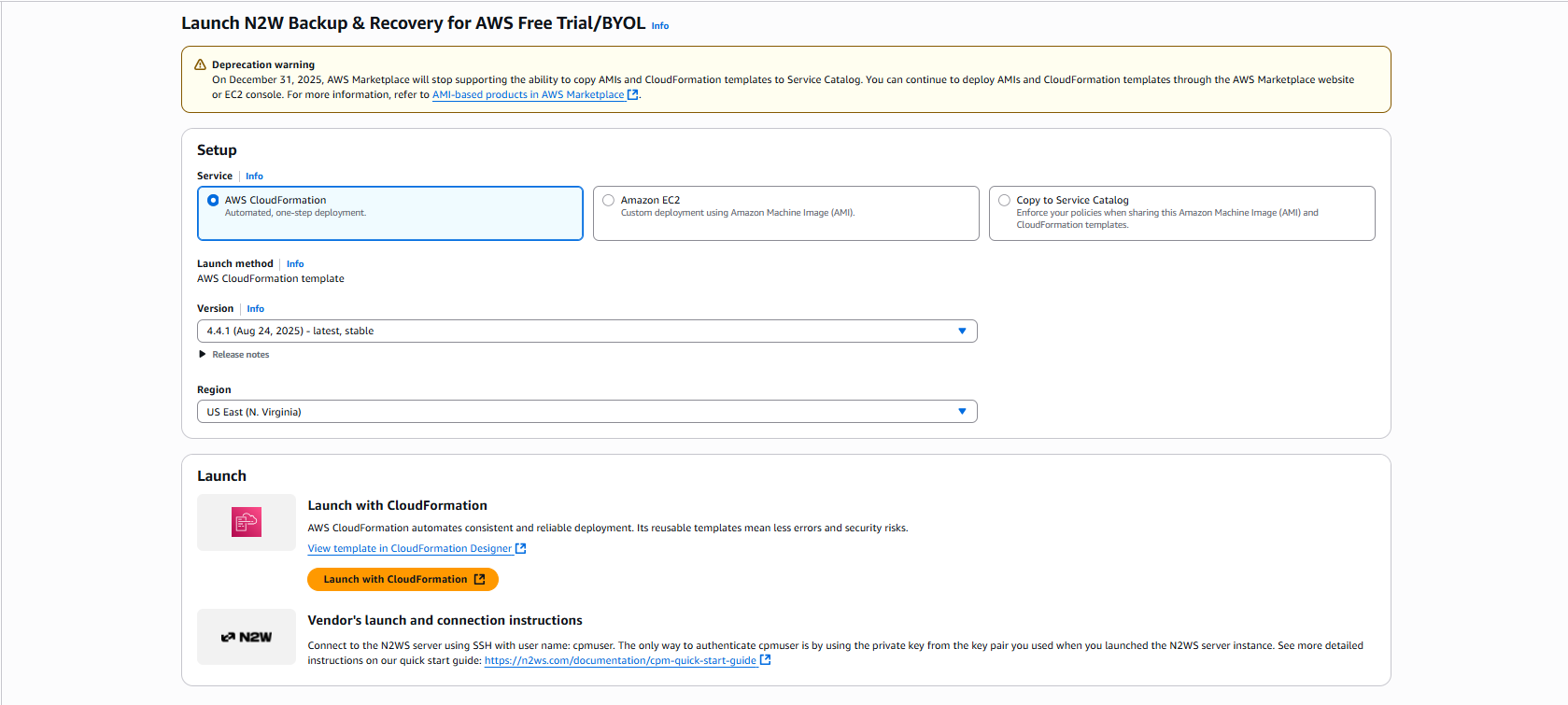
7. In the Create Stack page:
a. In the Prerequisite - Prepare template section, select Choose an existing template.
b. In the Specify template section, select Amazon S3 URL. In the Amazon S3 URL window, the address of the template will appear.
c. Select View in Infrastructure Composer.
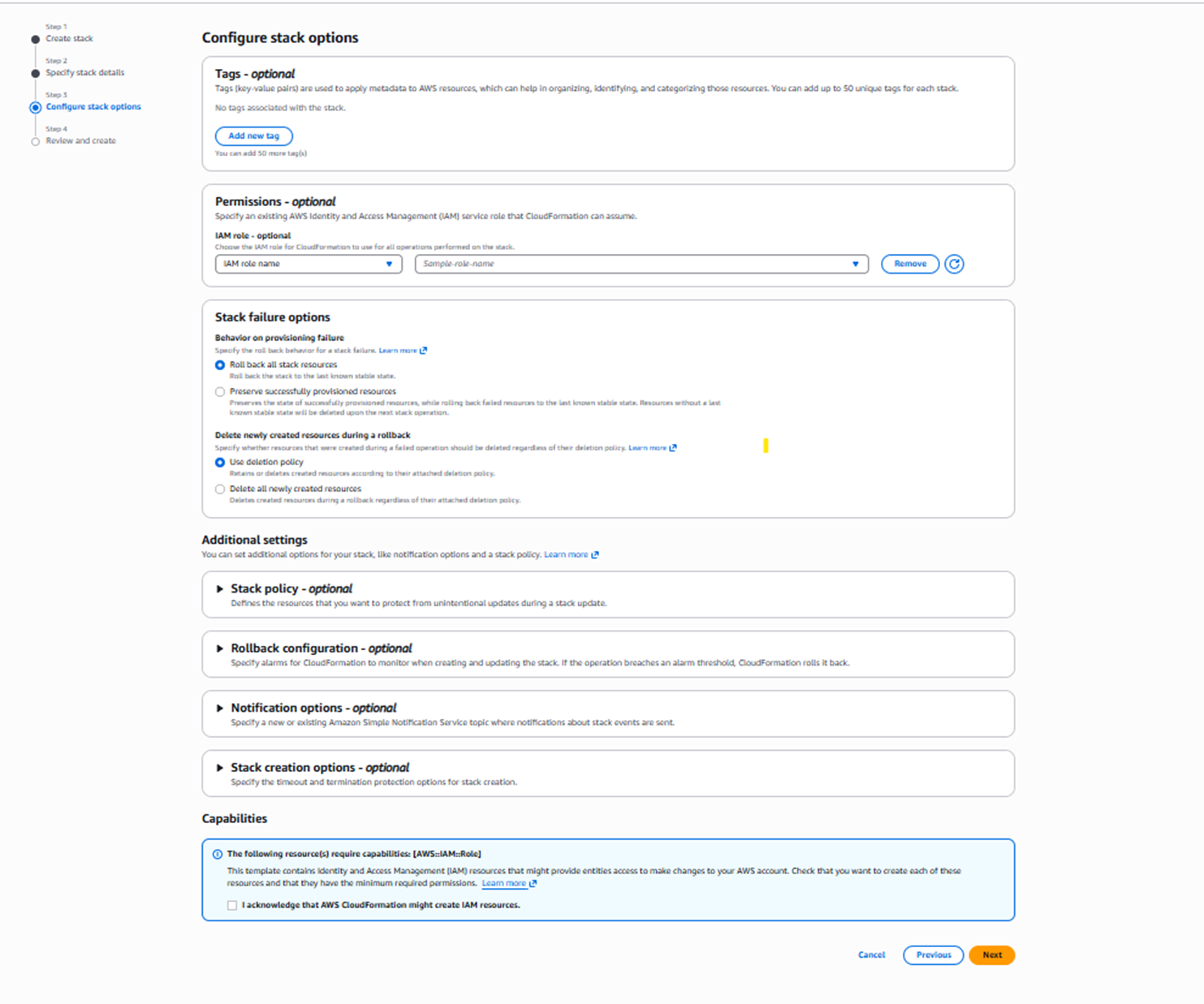
8. Select Next. The Configure stack options page opens.
a. If needed, select Add new tag.
b. In the Capabilities section, select I acknowledge that AWS CloudFormation might create IAM resources.
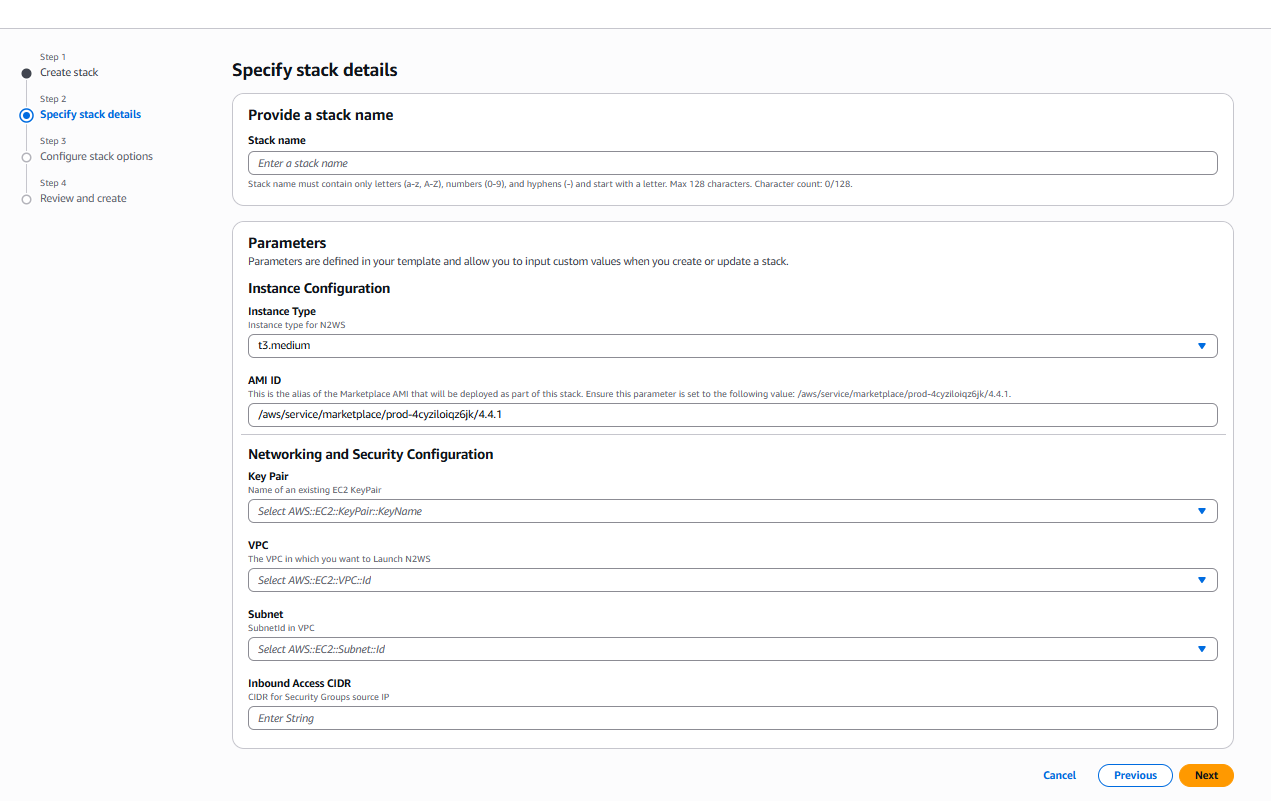
9. Select Next. The Specify stack details page opens. Provide a stack name and parameters.
For Inbound Access CIDR, security groups act as a firewall for associated instances, controlling both inbound and outbound traffic at the instance level. Configuring Inbound Access CIDR allows you to add rules to a security group that enable you to connect to your Linux instance from your IP address using SSH:
If your IPv4 address is 203.0.113.25, specify 203.0.113.25/32 to list this single IPv4 address in CIDR notation.
If your company allocates addresses within a range, specify the entire range, such as 203.0.113.0/24.
If you specify 0.0.0.0/0, it will enable all IPv4 addresses to access your instance using SSH.
For further details, refer to “Adding a Rule for Inbound SSH Traffic to a Linux Instance” at https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/authorizing-access-to-an-instance.html
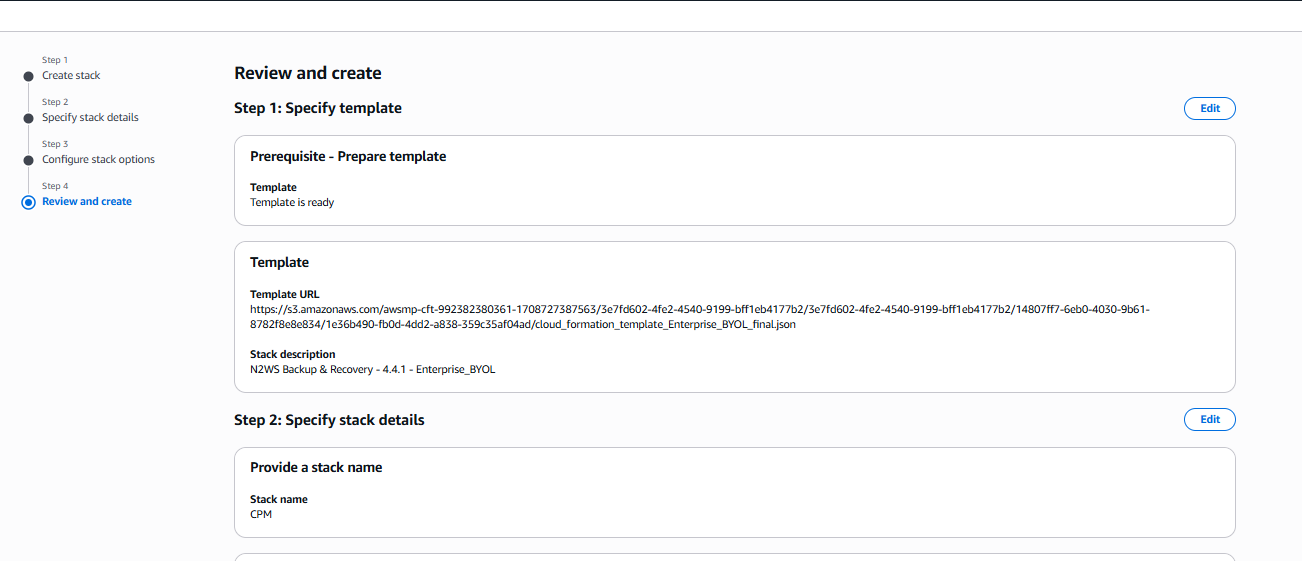
Select Next. The Review and create page opens. Review and edit as necessary.
Step 1, Specify template, and Step 2, Specify stack details:
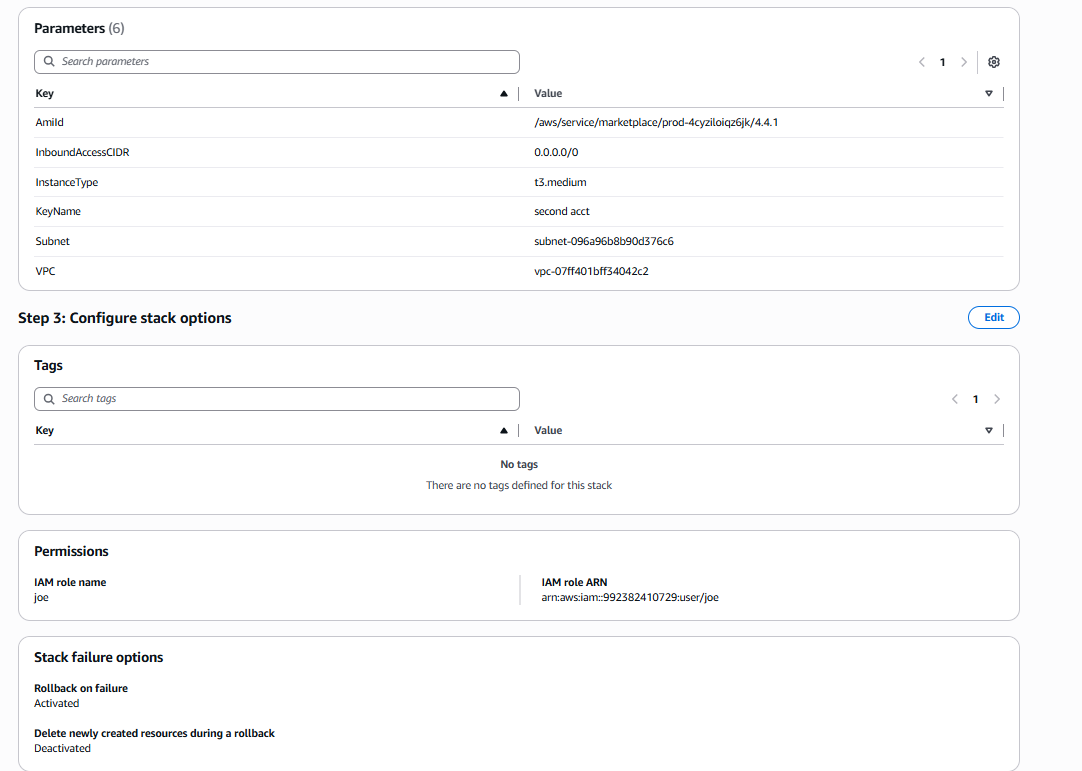
b. Step 2, Parameters, and Step 3 Configure stack options, such as Tags and Permissions:
c. Step 3, Stack failure options, Stack policy, and Rollback configuration:
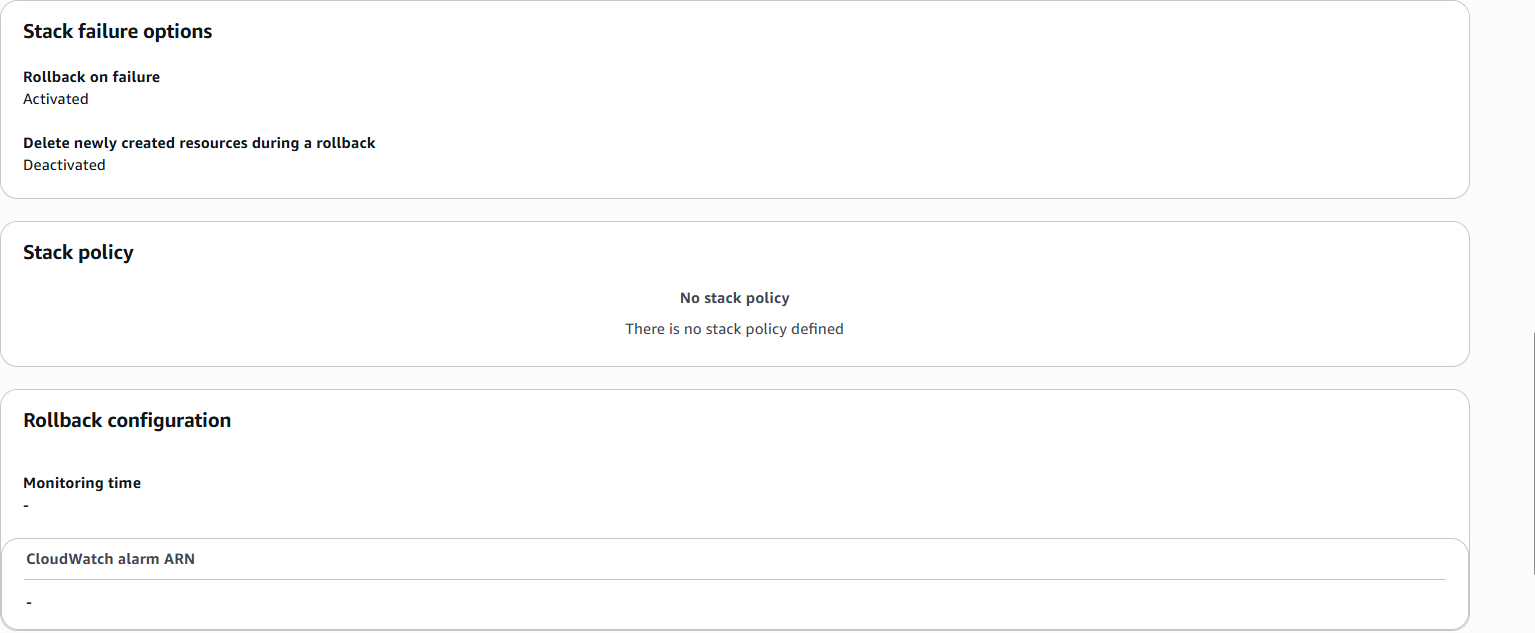
d. Step 3, Notification options, Stack create options, and Quick-create link:
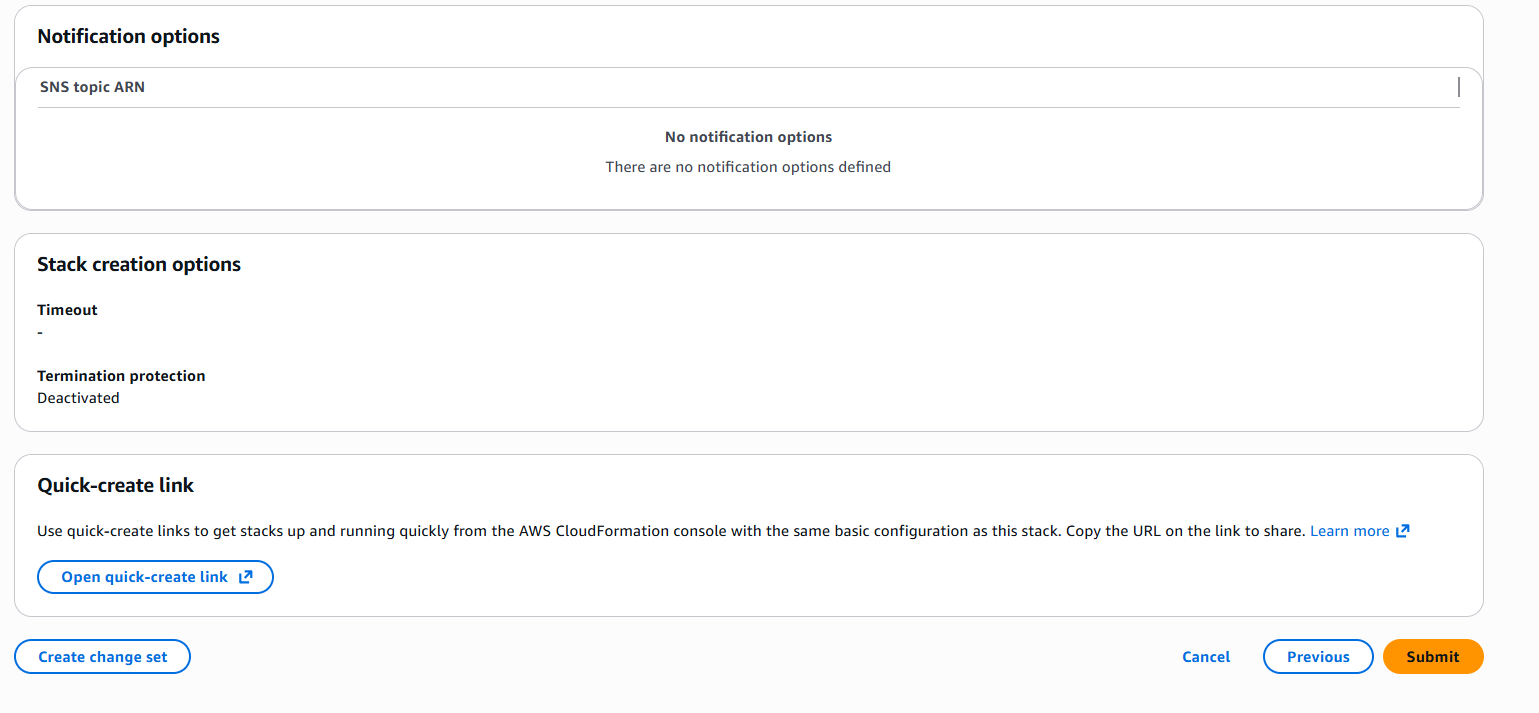
After all sections are reviewed, select Submit. The last configuration page opens, where you can observe the progress of the stack creation.
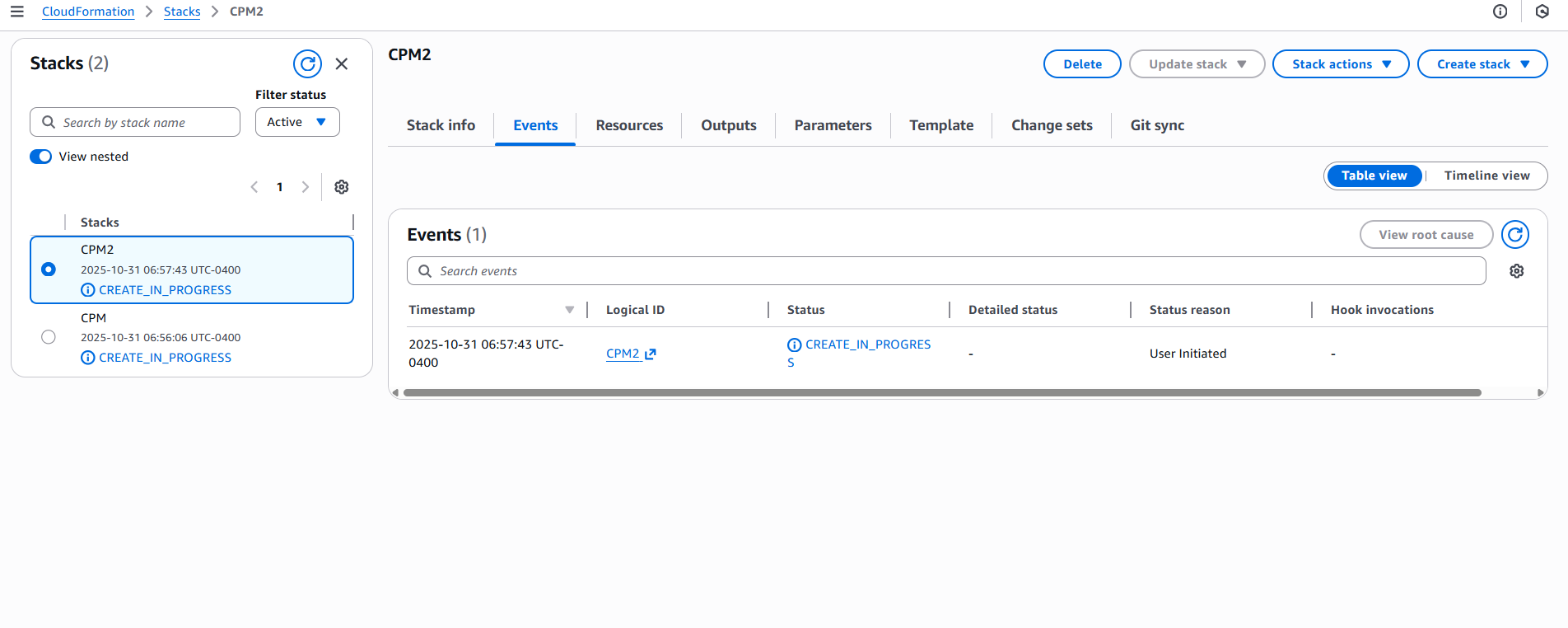
12. Continue configuring N2W as in section 2.
Was this helpful?

