16 Security Concerns and Best Practices
Understand how to create the optimum security profile for your system.
Security is one of the main issues and barriers in decisions regarding moving business applications and data to the cloud. The basic question is whether the cloud is as secure as keeping your critical applications and data in your own data center. There is probably no one simple answer to this question, as it depends on many factors.
Prominent cloud service providers like Amazon Web Services, are investing a huge number of resources so people and organizations can answer ‘yes’ to the question in the previous paragraph. AWS has introduced many features to enhance the security of its cloud. Examples are elaborate authentication and authorization schemes, secure APIs, security groups, IAM, Virtual Private Cloud (VPC), and more.
N2W strives to be as secure as the cloud it is in. It has many features that provide you with a secure solution.
16.1 N2W Server
N2W Server’s security features are:
Since you are the one who launches the N2W server instance, it belongs to your AWS account. It is protected by security groups you control and define. It can also run in a VPC.
All the metadata N2W stores are stored in an EBS volume belonging to your AWS account. It can only be created, deleted, attached, or detached from within your account.
You can only communicate with the N2W server using HTTPS or SSH, both secure protocols, which means that all communication to and from N2W is encrypted. Also, when connecting to AWS endpoints, N2WS will verify that the SSL server-side certificates are valid.
Every N2W has a unique self-signed SSL certificate. It is also possible to use your own SSL certificate.
AWS account secret keys are saved in an encrypted format in N2W’s database.
N2W supports using different AWS credentials for backup and recovery.
N2W Server supports IAM Roles. If the N2W Server instance is assigned an adequate IAM role at launch time, you can use cross-account IAM roles to “assume” roles from the main IAM role of the N2W instance account to all the other AWS accounts you manage and not type AWS credentials at all.
To manage N2W, you need to authenticate using a username and password.
N2W allows creating multiple users to separately manage the backup of different AWS accounts, except in the Free Edition.
16.2 Best Security Practices for N2W
Implementing all or some of the following best practices depends on your company’s needs and regulations. Some of the practices may make the day-to-day work with N2W a bit cumbersome, so it is your decision whether to implement them or not.
16.2.1 Avoid using AWS Credentials
By using the N2W Server instance IAM role and cross-account IAM role, you can manage multiple AWS accounts without using AWS credentials (access and secret keys) at all. This is the most secure way to manage multiple AWS accounts and the one recommended by AWS.
16.2.2 Credential Rotation
Assuming you have to use AWS credentials, you should follow AWS practices. N2W recommends that you rotate account credentials from time to time.
After changing credentials in AWS, you need to update them in N2W. Select on the account name in the Accounts management screen and modify the access and secret keys.
16.2.3 Passwords Rules and Expiration
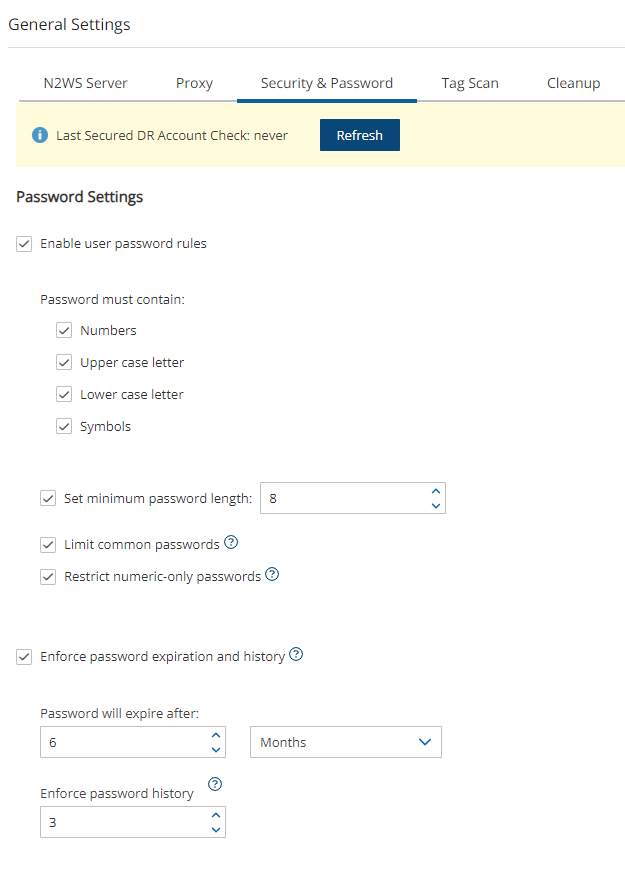
To improve user security and align with current password practices, the N2W root user can enforce password rules and password expiration. Both are optional and can be enabled or disabled through Security settings.
Password settings allow the root user to enforce password rules on all N2W users (including the root user himself), to define the period for password expiration, and to enforce password expiration.
The default is to enable password rules and password expiration for 6 months.
Default password rules and expiration settings can be disabled by clearing their respective Enable/Enforce check boxes.
Password settings are enforced throughout N2W.
If you upgrade from 4.0.0c version and below, the password age will be counted on the day of upgrade.
To set password rules, expiration, and history limit:
In
 Server Settings in the top right toolbar, select General Settings, and then select the Security & Password tab.
Server Settings in the top right toolbar, select General Settings, and then select the Security & Password tab.In the Password Settings section, if you want to disable the default enforcement of the password roles, clear the Enable user password rules check box.
If you didn’t disable the default password rules, change the various default rule options as necessary:
Password must contain certain characters.
Set minimum password length. Default is 8.
Limit common passwords. Passwords are matched against a list of 20,000 common passwords.
Restrict numeric-only passwords.
If you want to disable the default enforcement of password expiration and history, clear the Enforce password expiration and history check box.
If you didn’t disable the default enforcement of the password expiration and history, change the various default expiration and history options as necessary:
Password expiration in terms of duration.
Limit of number of passwords to be included in history. Default is 3, maximum is 10.
If history value is 3, users can’t reuse any of their last 3 passwords.
Password Enforcement
Password rules are enforced throughout all N2W functions and features:
Configuration Wizard
User/Delegate creation
Reset Password (by root user)
Change Password (by the user itself)
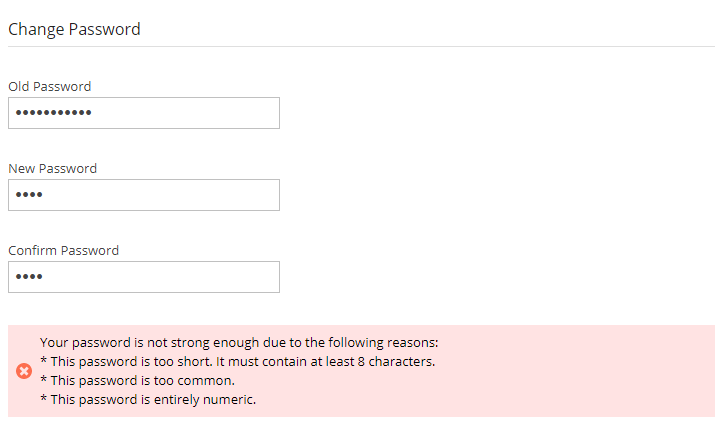
In the following example, a user attempted to change their password to ‘1234’, which breaks all password rules:
Password Expiration
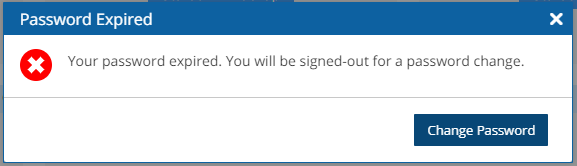
When the password expires, the user will see the following message after login. The user will then be transferred to a password change page.
16.2.4 Automatic Logout
Setting an automatic logout is another security best practice. Setting a Login Session Expiration value handles automatic logout from N2W Backup & Recovery.
To set the time for automatic logout:
In
 Server Settings in the top right toolbar, select General Settings tab, and then select the Security & Password tab.
Server Settings in the top right toolbar, select General Settings tab, and then select the Security & Password tab.In the Login Session Expiration section, select the time after which the user is to be logged out.
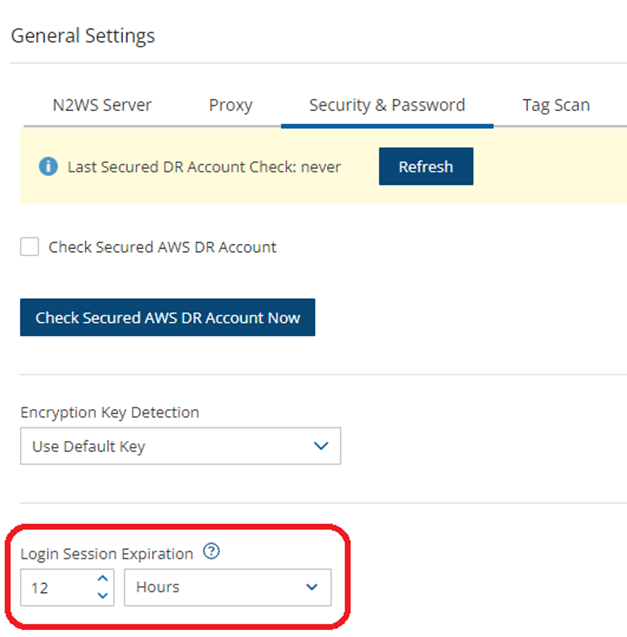
The default logout is after 12 hours of mouse and keyboard being idle. The minimum expiration time is 3 minutes.
16.2.5 Security Groups
Since the N2W server is an instance in your account, you can define and configure its security groups. Even though N2W is a secure product, you can block access from unauthorized addresses:
You need HTTPS access (original 443 port or your customized port) from:
Any machine which will need to open the management application
Machines that have N2W Thin Backup Agent installed on them. See section 6.1.
You will also need to allow SSH access to create and maintain backup scripts.
Blocking anyone else will make N2W server invisible to the world and therefore completely bullet-proof.
The only problem with this approach is that any time you will try to add new backup agents or connect to the management console or SSH from a different IP, you will need to change the settings of the security groups.
Learn more about AWS Security Groups and settings at https://docs.aws.amazon.com/vpc/latest/userguide/VPC_SecurityGroups.html
16.3 Using IAM
N2W keeps your AWS credentials safe. However, it is preferable to use IAM roles and not use credentials at all. Additionally, N2W will not accept root user credentials. To minimize risk, try:
To provide credentials that are potentially less dangerous if they are compromised, or
To set IAM roles, which will save you the need of typing in credentials at all.
You can create IAM users/roles and use them in N2W to:
Create a user/role using IAM.
Attach a user policy to it.
Use the policy generator to give the user custom permissions.
Using IAM User credentials is not recommended as they are less secure than using IAM roles.
An IAM role can also be used in the N2W Server (for the account the N2W Server was launched in) and for instances running N2W Agent to perform the configuration stage as well as normal operations by combining some of the policies. You can attach more than one IAM policy to any IAM user or role.
The permissions that the IAM policy must have depend on what you want to policy to do. For more information about IAM, see IAM documentation: http://aws.amazon.com/documentation/iam/
16.3.1 N2W Server Configuration Process
AWS credentials in the N2W configuration process are only used for configuring the new server. However, if you want to use IAM credentials for the N2W configuration process, or to use the IAM role associated with the N2W Server instance, its IAM policy should enable N2W to:
View volumes instances, tags, and security groups
Create EBS volumes
Attach EBS volumes to instances
Create tags
Generally, if you want to use IAM role with the N2W Server instance, you will need the following policy and the policies for N2W Server’s normal operations, as described in section 16.3.2.
Minimal IAM Policy for N2W Configuration:
16.3.2 N2W Server IAM Settings
You can use the N2W Server’s IAM role to manage backups of the same AWS account. If you manage multiple AWS accounts, you will still either need to create cross-account roles or enter the credentials for other accounts. If you want to use an IAM user for an account managed by N2W Server (or the IAM role), you need to decide whether you want to support backup only or recovery as well. There is a substantial difference:
For backup, you only need to manipulate snapshots.
For recovery, you will need to create volumes, create instances, and create RDS databases. Plus, you will need to attach and detach volumes and even delete volumes. If your credentials fall into the wrong hands, recovery credentials can be more harmful.
If you use a backup-only IAM user or role, then you will need to enter ad hoc credentials when you perform a recovery operation.
Generally, if you want to use the IAM role with the N2W Server instance, you will need a certain policy, or policies, for N2W Server’s normal operations. For AWS, see https://n2ws.zendesk.com/hc/en-us/articles/33252616725533--4-5-0-Required-Minimum-AWS-permissions-for-N2W-operations
Using IAM User credentials is not recommended as they are less secure than using IAM roles.
You can check on the permissions required for AWS services and resources, such as backup, RDS, and DynamoDB, and compare them to the policies that cover the requirements.
Limitation: In certain circumstances, the permissions checker may evaluate IAM entities incorrectly, due to limitations on the AWS side. This is especially likely when Service Control Policies (SCPs) are applicable to the account.
In the Accounts tab, select an account and then select ![]() Check AWS Permissions. To expand a line, select its down arrow
Check AWS Permissions. To expand a line, select its down arrow ![]() .
.
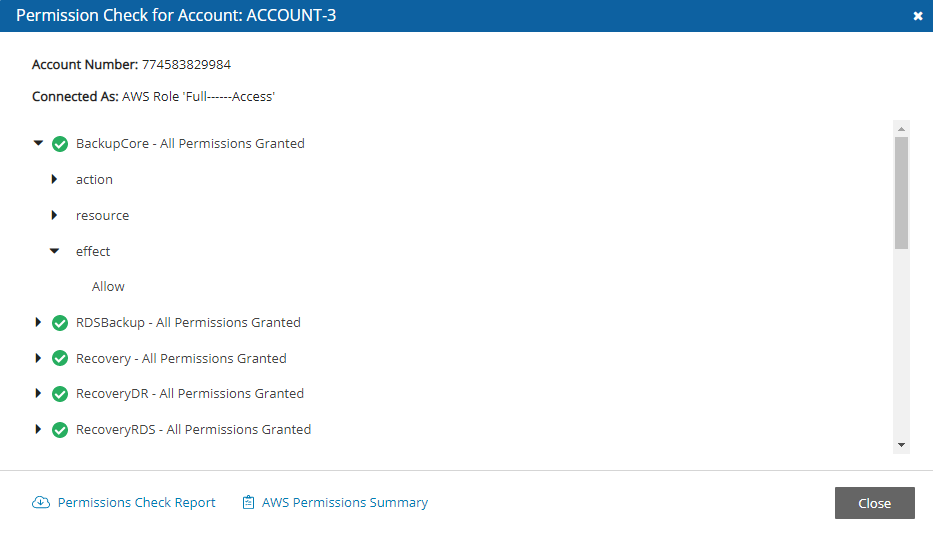
To download a CVS report, select
 Permissions Check Report.
Permissions Check Report.To download a JSON file, select
 AWS Permissions Summary.
AWS Permissions Summary.
16.3.3 Configure N2W’s IAM Role with CloudFormation
CloudFormation is an AWS service that allows you to treat a collection of AWS resources as one logical unit. CloudFormation provides a common language for you to describe and provision all the infrastructure resources in your cloud environment, across all regions and accounts in an automated and secure manner.
The IAM role will automatically contain the required permissions for N2W operations. See section 20.
Last updated
Was this helpful?

