23 Capturing and Cloning in Network Environments
In this section, you will learn how to use a Amazon Virtual Private Cloud (VPC) to launch AWS resources into a logically separate virtual network.
The capturing and cloning of Network Environments (VPCs, Transit Gateways, and Load Balancers (LBs)) is not available with the Free edition of N2W.
23.1 Overview of VPC and N2W
VPC is an AWS service that allows the definition of virtual networks in the AWS cloud. Users can define VPCs with a network range, define subnets under them, security groups, Internet Getaways, VPN connections, and more. One of the resources of the VPC service is also called ‘VPC’, which is the actual virtual, isolated network.
N2W can capture the VPC and Transit Gateway settings as root resources, including their related resources of user environments and clone those settings back to AWS:
In the same region and account, for example, if the original settings were lost.
To another region and/or account, such as in DR scenarios.
With VPC resource properties modified in template uploaded with CloudFormation, if required.
23.2 Overview of LBs and N2W
LBs are located under the EC2 AWS service. Users can define LBs with Listeners and Target Groups. Following are the types of LBs:
Classic
V2 which includes subtypes Application, Network and Gateway.
N2W can capture LBs of all types, including their related resources and clone those settings back to AWS:
In the same region and account, for example, if the original settings were lost.
To another region and/or account, such as in DR scenarios.
With LB resource properties modified in a template uploaded with CloudFormation, if required.
Once enabled from General Settings, N2W will automatically capture network environment settings at pre-defined intervals, such as for cleanup and tag scanning. The root/admin user can enable the feature in the Capture Network Environments tab of the General Settings screen and set the interval of captures. Capture settings are enabled at the account level, by default, same as tag scanning.
Because Network Environment configuration metadata is small, it does not consume a lot of resources during storage of the capture. Metadata is captured incrementally. If nothing changed since the last capture, the metadata will not be captured again. This is the most common case in an ongoing system, where defined networks do not change frequently.
Regions - N2W will only capture Network Environment settings in regions that include backed-up resources. If the customer is not backing up anything in a specific region, N2W will not try to capture the VPC settings there.
Retention - N2W will retain the Network Environment data if there are backups requiring it. If N2W still holds backups from a year ago, the capture version relevant for that time is still retained. Once there are no relevant backups, N2W will delete the old captured data.
CloudFormation - N2W will use the AWS CloudFormation service to clone a Network Environment’s root entities (VPCs, Transit Gateways, and LBs) to an AWS account and region. N2W will create a CloudFormation template with the definitions for the entities and use the template to launch a new stack and create all the settings of the root entities in one operation.
23.3 Features of Capturing and Cloning Network Environments
Limitations:
On Transit Gateways, attachments of type 'Direct Connect Gateways' are not supported.
Transit Gateway Policy Tables are not supported.
Capturing and cloning Transit Gateways in the following regions is not supported: China regions, Government regions, Jakarta, and Osaka.
The clone destination region should have sufficient quotas to hold all resources captured in the source region.
Shared Resource Limitations:
The following shared resources are not supported for cloning:
Shared Prefix lists
Shared Subnets
Shared Transit Gateway Multicast Domains
A shared Transit Gateway is supported only if the account providing the shared access is defined as a ‘CPM account’.
The clone of a Transit Gateway shared with a different account will be cloned to only one target account even though the original Transit Gateway was spread over 2, or more, AWS accounts.
The objective of Capture and Clone is to provide the ability to protect the root entities of Network Environment types (VPCs, Transit Gateways, and LBs) from disaster, by saving their configurations and allowing for recovery in any region.
Backed up VPC entities include:
VPC resource configuration
Subnets - N2W tries to match AZs with similar names and spread subnets in destinations in the same way as in source regions.
Security groups
DHCP Options Sets - Not supporting multi-name in domain server name.
Route tables - Not supporting rules with entities that are specific to the source region.
Network ACLs
Internet Gateways
Egress-Only Internet Gateways
VPN Gateways
Customer Gateways
VPN Connections
NAT Gateways
VPC Peering connections - Not supporting peer on a different AWS account
Managed Prefix Lists
The Capture Log in the Capture Network Environments tab of General Settings reports the capture status of entities: captured, not captured, or only partially captured.
Backed up Transit Gateway entities include:
Transit Gateway resource configuration
Related VPCs and related resources to VPC - See above.
Transit Gateway attachments:
VPC
VPN
Peering Connection - Requires accepting connection on Peer
Connect
Transit Gateway Route Tables
Transit Gateway Multicast Domains
Related Network Interfaces
Custom Gateways
VPN Connections
NAT Gateways
VPC Peering connections - Not supporting peer on a different AWS account.
Managed Prefix Lists
Backed up LB entities include:
Related VPCs and their resources. See above.
Target Groups
Listeners
Network Environment capturing:
Accounts are enabled for Network Environment configuration capturing by default, but this setting can be disabled as needed.
Captures in all regions of interest, excluding the unsupported regions.
N2W will capture and save all changes made on AWS for a user’s VPCs, Transit Gateways, and LBs.
Not supported: Carrier gateways, Network interfaces related to VPCs, Elastic IP addresses, VPC Endpoints, VPC Endpoints services, Firewalls, and Traffic Mirroring.
23.4 Updating Accounts for Capturing Network Environments
By default, Accounts are enabled to Capture Network Environment environment data. Configuration data is a automatically captured for all enabled Accounts according to the interval configured in the General Settings. To not Capture Network Environments for an Account, disable the feature in the Account.
To disable, or enable, an individual account for capturing Network Environments:
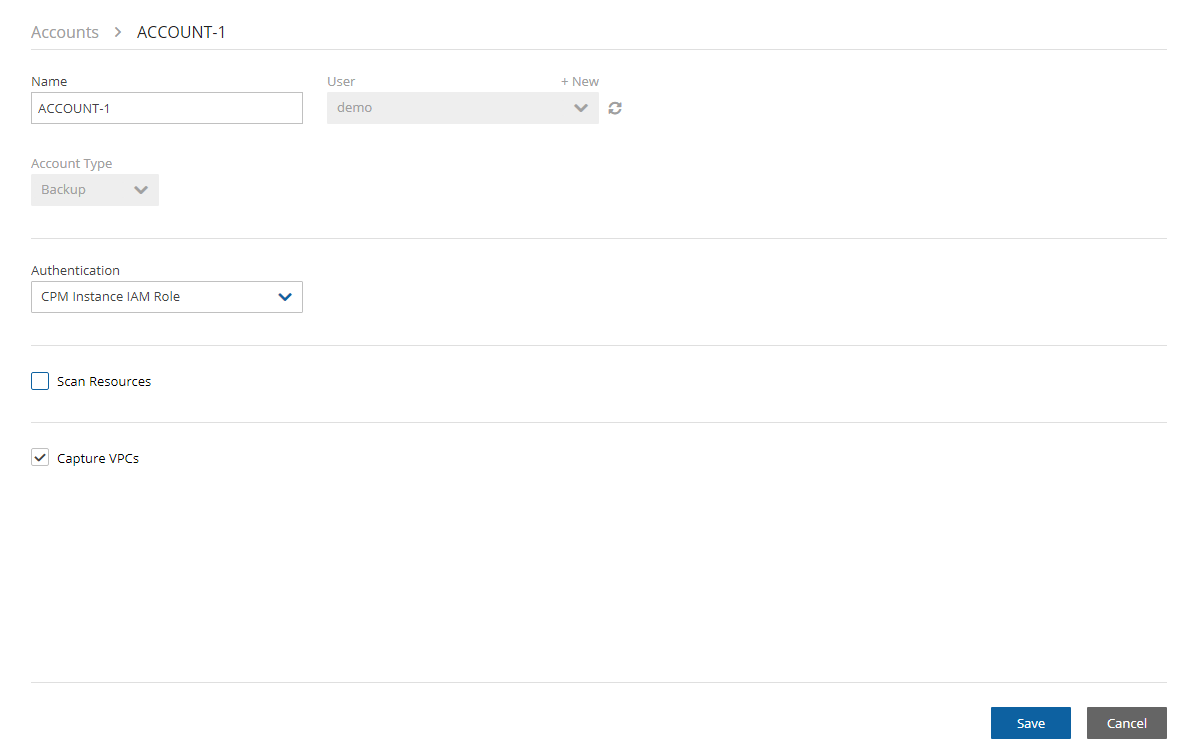
Select the Accounts tab, and then select an Account.
Select
 Edit.
Edit.Select Capture Network Environments to enable, or clear to disable.
Select Save.
23.5 Configuring Capture of Network Environment Entities
The root user can:
Enable or disable automatic capture of Network Environment entities for Accounts with the feature enabled.
Schedule automatic capture interval.
Initiate an ad hoc capture by selecting Capture Now for all Accounts with this feature enabled, even if Network Environments is disabled in General Settings.
View the last Network Environment entities captured in the different regions and accounts in Show Log.
Select
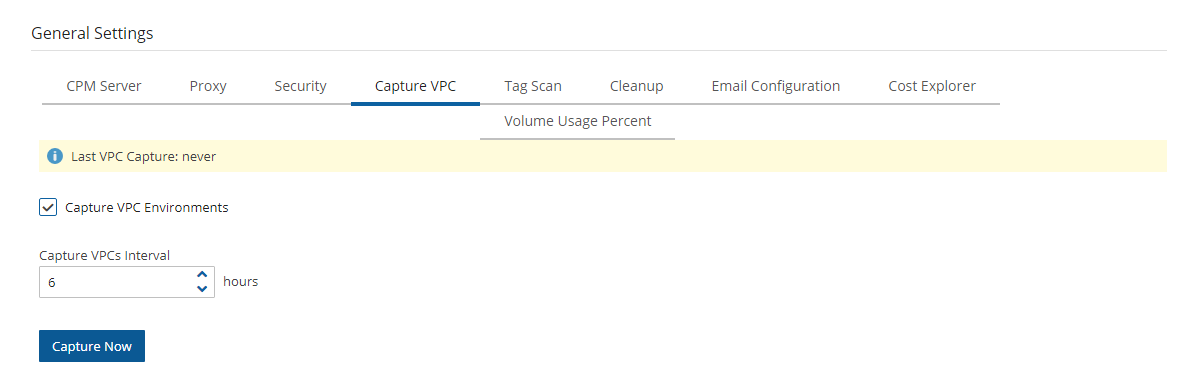
 Server Settings > General Settings.
Server Settings > General Settings.In the Capture Network Environments tab, select Capture Network Environments to enable the feature.
To change the capture frequency from the default, select a new interval from the Capture Interval list. Valid choices are from every hour to every 24 hours.
Select Save to update N2W.
To initiate an immediate capture for all Network Environment-enabled Accounts regardless of server setting, select Capture Now.
23.6 Cloning VPCs, Transit Gateways, and LBs
Cloning Network Environment entities include the following features:
Both cross-region and cross-account cloning are supported for VPCs, Transit Gateways, and LBs.
The target clone can have a new name. The name will automatically include ‘Clone of ’ at the beginning.
23.6.1 Cloning VPCs
The following entities are not supported:
Inbound and Outbound Endpoint rules of Security Groups.
Inbound and Outbound rules of Security Groups that refer to a security group on a different VPC.
Route Table rules with NAT Instance as target.
Route Table rules with Network Interface as target.
Route Table rules with VPC peering connection as target.
Route Table rules with status 'Black Hole'.
Prerequisites, Conditions, and Limitations
Before cloning, verify that the destination region has sufficient quotas for all resources captured in the source region.
Cloning a VPN connection with an Authentication type other than 'Pre Shared Keys' is not supported. Attempting to clone this VPN connection requires manually replacing it after cloning.
When cloning a VPC Peering Connection, the accepter VPC must exist in the peer destination region. Download and edit the CloudFormation template.
When cloning a NAT Gateway with public connectivity, the Elastic IP allocation ID must exist and be available. Download and edit the CloudFormation template.
When cloning includes a Customer Gateway, if the original Customer Gateway exists, it will be used; otherwise, it will be created.
Cloning a VPC Peering connection with a VPC peer on a different AWS account is not supported. Download and edit the CloudFormation template.
An account with Capture Network Environments enabled must have at least one policy with a backup target to clone Network Environment entities. If no backup target is configured, the Network Environment entities will not be captured even if Enable Network Capture is enabled.
Cloning VPCs includes the following features:
The target clone can have a new name. The name will automatically include ‘Clone of’ at the beginning.
During instance recovery and DR, clones may be optionally created to replicate a particular VPC environment before the actual instance recovery proceeds. The new instance will have the environment of the cloned VPC and will subsequently appear at the top of the target region and account list. A typical scenario might be to capture the VPC, clone the VPC for the first instance, and then apply the cloned VPC to additional instances in the region/account.
Instances recovered into a cloned VPC destination environment will also have new default entities, such as the VPC’s subnet definition and 1 or more security groups attached to the instance, regardless of the original default entities. Security groups can be changed during recovery.
23.6.2 Cloning Transit Gateways
The following item is not supported:
Capturing and Cloning Transit Gateways on the following regions is not supported: Osaka, Jakarta, the Government regions, and China regions.
Instructions and limitations:
You can reuse the existing VPCs related to the Transit Gateway by selecting the relevant check box on the Clone page.
It is not possible to clone a Transit Gateway where the number of unique AZ references in the resources is greater than the number of AZs in the Clone region. Download and edit the CF template.
Transit Gateway peer attachment is not supported if cloned Transit Gateway is an Accepter and not a Requester.
If the original Transit Gateway had ‘DefaultRouteTableAssociation’ and/or ‘DefaultRouteTablePropagation’ in ‘enable’ state, on the cloned Transit Gateway, it will be ‘disable’. Change the flag 'enable' and choose default Route Table on VPC Console.
Cloning routes Propagation/Association of VPN to Route Table is not supported. Manually add the missing routes on VPC Console.
Cloning of Managed Prefix List references of Transit Gateway Route Table is not supported. Manually add the missing details on VPC Console.
The downloaded Clone log will indicate that a reference is required to be made manually.
The Transit Gateway Route Table that requires a reference to a Managed Prefix List will have a Tag pointing to the Prefix list to reference.
The cloned Managed Prefix List that needs to be referenced will also indicate the referencing Transit Gateway Route Tables entity.
Transit Gateway Connect Peer that is related to Connect Transit Gateway attachment is not supported. Manually add the missing details on VPC Console.
When cloning includes a Customer Gateway – if the original Customer Gateway exists, it will be used, otherwise, it will be created.
If a related VPC is cloned (i.e., the existing VPCs were not reused) and the original includes VPN Connections, you will need to re-establish the connections using the new configuration for the VPN tunnels..
An account with Capture Network Environments enabled must have at least one policy with a backup target for cloning Network Environment entities.
26.6.3 Cloning LBs
Instructions and limitations:
You can reuse the existing VPCs related to the LB by selecting the related check box on the Clone page. When selected, you can choose whether to attach the existing original instances to the cloned LB.
It is not possible to clone an LB where the number of unique AZ references in the resources is greater than the number of AZs in the Clone region. Download and edit the CF template.
If a related VPC is cloned (i.e., the existing VPCs were not reused) and the original includes VPN Connections, you will need to re-establish the connections using the new configuration for the VPN tunnels.
Lambda function permissions: If the captured LB includes a listener that forwards to a Lambda Target Group, the following are issues to consider before cloning:
Manually add the permission: "lambda:AddPermission" to the relevant IAM policy.
The 'lambda:InvokeFunction' permission will be added to the existing Lambda function during cloning.
On a Classic LB clone, the Policy may not have information such as Instance Ports or LB Ports that can’t be cloned due to CloudFormation limitations. The missing data is indicated in the clone’s Download Log.
On a V2 LB clone, the Listener’s tags are not cloned due to CloudFormation limitations. The missing data is indicated in the clone’s Download Log.
An account that has Capture Network Environments enabled must have at least one policy with a backup target to clone Network Environments entities.
23.6.4 The CloudFormation Template
When cloning Network Environment entities to an AWS account, N2W generates a JSON template for use with CloudFormation (CF).
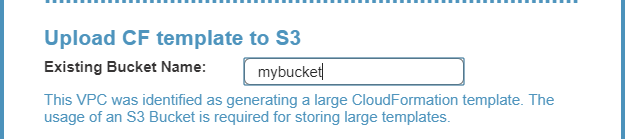
If the size of the CF template generated is over 50 kB, N2W requires the use of an existing S3 Bucket in the target destination for storing the template. There should be an S3 bucket for each combination of accounts and regions in the destination clone. The template file in a S3 bucket will not be removed after cloning.
In addition to having a bucket in the target region in the presented settings, you must choose that bucket when defining where to Upload the CF template to S3.
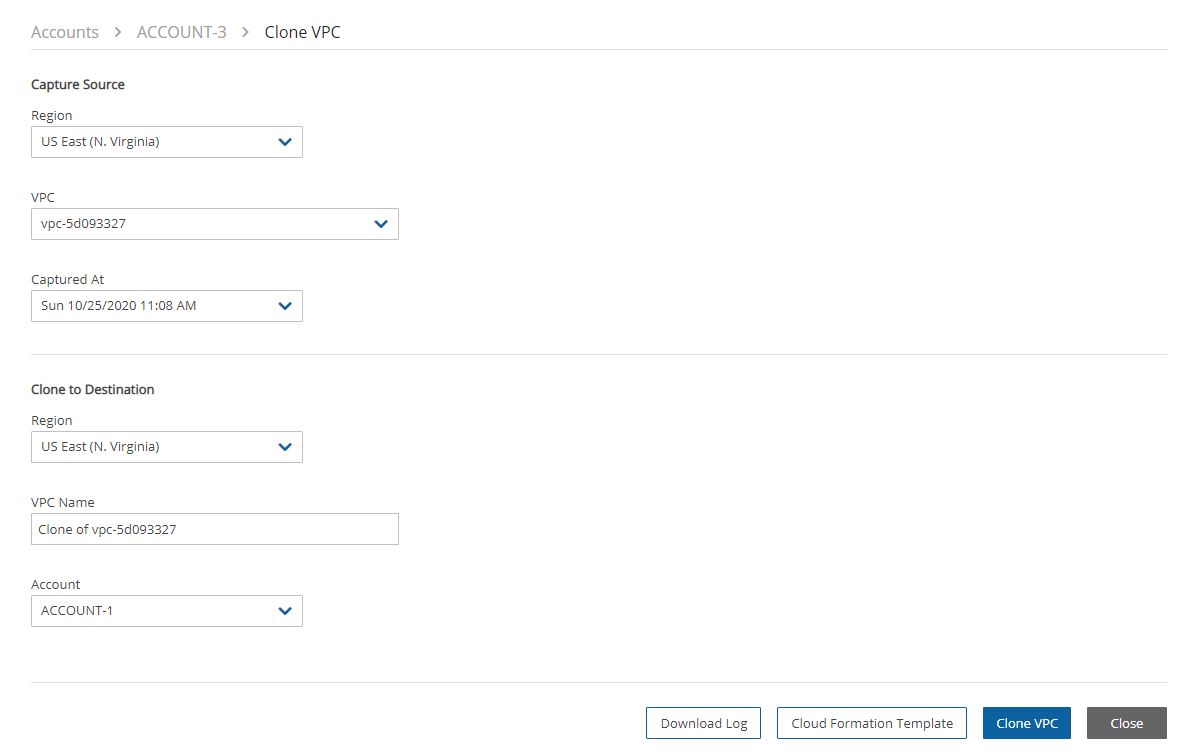
To clone captured VPCs, Transit Gateways, or LBs:
Select the Accounts tab and then select an account.
Select
 Clone Network Entities.
Clone Network Entities.In the Capture Source section Network Entity Type list, select VPC, Transit Gateway, or LB.
In the Capture Source section Region drop-down list, select the source region of the capture to clone.
In the Source VPC/Transit Gateway/LB drop-down list, select the item to clone.
In the Captured at drop-down list, select the date and time of the capture to clone.
In the Clone to Destination section Region drop-down list, select the region to create the clone.
In the VPC/Transit Gateway Name/LB box, a suggested name for the cloned item is shown. Enter a new name, if needed.
In the Account drop-down list, select the account in which to create the clone.
If the CF template is over 50 kB, in the Upload CF template to S3 dialog box, enter the name of an S3 bucket that exists in the selected target region.
If the Network Entity Type is Transit Gateway or Load Balancer, you can choose whether to reuse existing VPCs.
If the Network Entity Type is LB and reuse existing VPCs is enabled, you can choose whether to attach the original existing instances to the cloned LB.
Select Clone VPC/Clone Transit Gateway/Clone LB. At the end of the cloning, a status message will appear in a box:
Cloning VPC/Transit Gateway/LB completed successfully. There may be an informational message that you may need to make manual changes. Check the log, using Download Log, for further information.
To view the results of the clone network entity action, select Download Log.
When cloning VPCs. Transit Gateways, or LBs with resources not supported by N2W, you can download the CloudFormation template for the cloned entity, add or modify resource information, and upload the modified template to the AWS CloudFormation service manually.
To create a clone manually with CloudFormation:
In the Account Clone Network Entities screen, complete the fields as described above.
Select VPC/Transit Gateway/LB CloudFormation Template to download the CloudFormation JSON template.
Modify the template, as required. See the example in section 23.6.5.
Manually upload the modified template with CloudFormation.
23.6.5 Example of CloudFormation Template
Was this helpful?

